2024CISCN初赛 Reverse
最近太忙了,终于等pycc搞完,有点时间,进行赛后复现一下
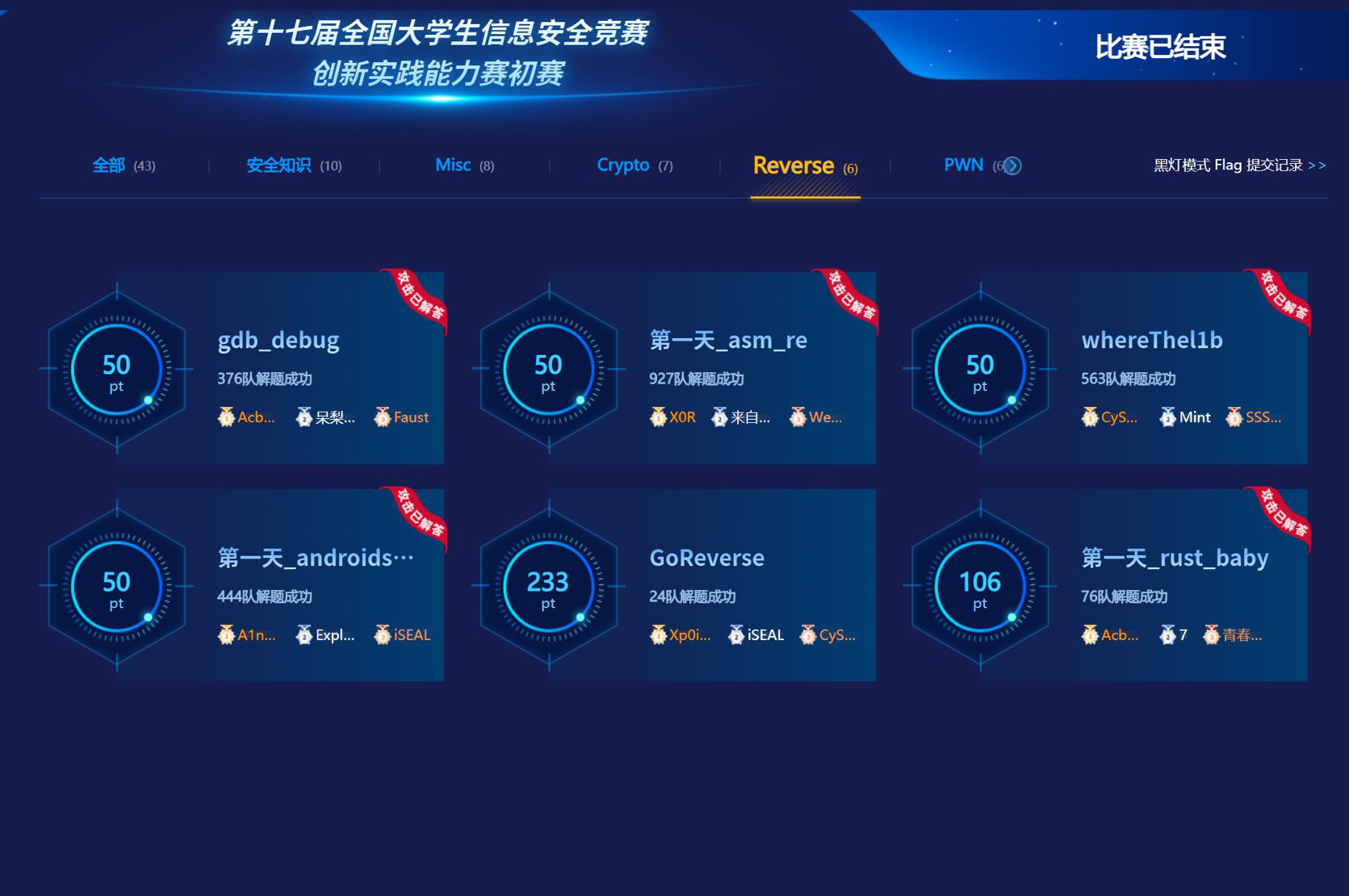
可惜了差道Goreverse,还需再练练,除了安卓其他题都出的挺好的
asm_re
汇编看得太慢了,不太熟练,直接取巧提取一下放ida里解析了
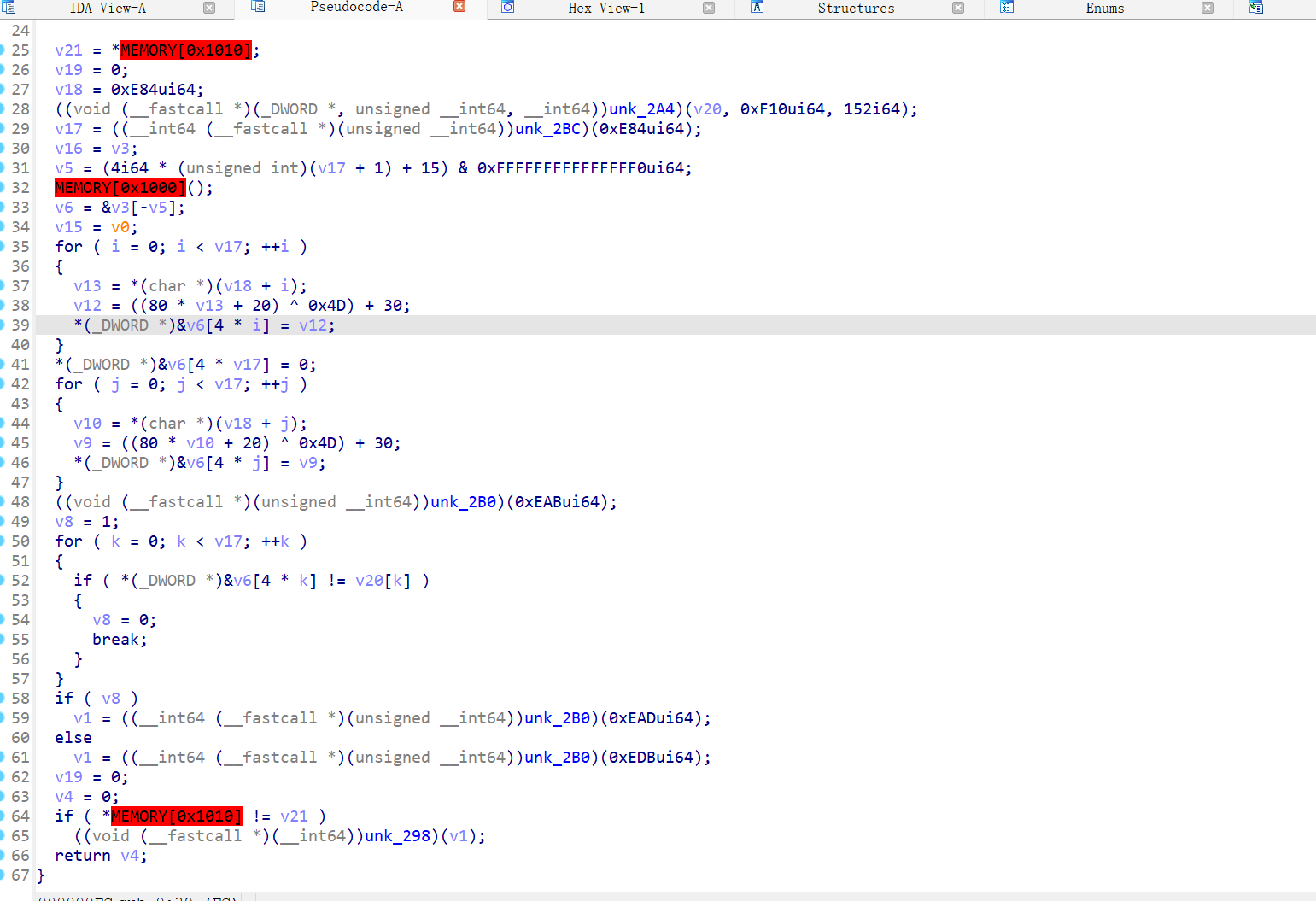
一个简单的*+^操作,当时还奇怪为什么是int类型的密文,现在知道了,第一天的签到
1 |
|
这种跟类型有关的题还是喜欢用c写
android_so
哎只允许真机调试,有点出的不好了,对于我这种模拟器玩家很是难做,借了个学长的真机穿。
java层就一个base+des-CBC,主要iv和key都放在了so层处理。
key能直接断在返回那边动调出
iv用个frida hook cypher.init脚本出
rust_baby
看代码看得最头疼的一题,
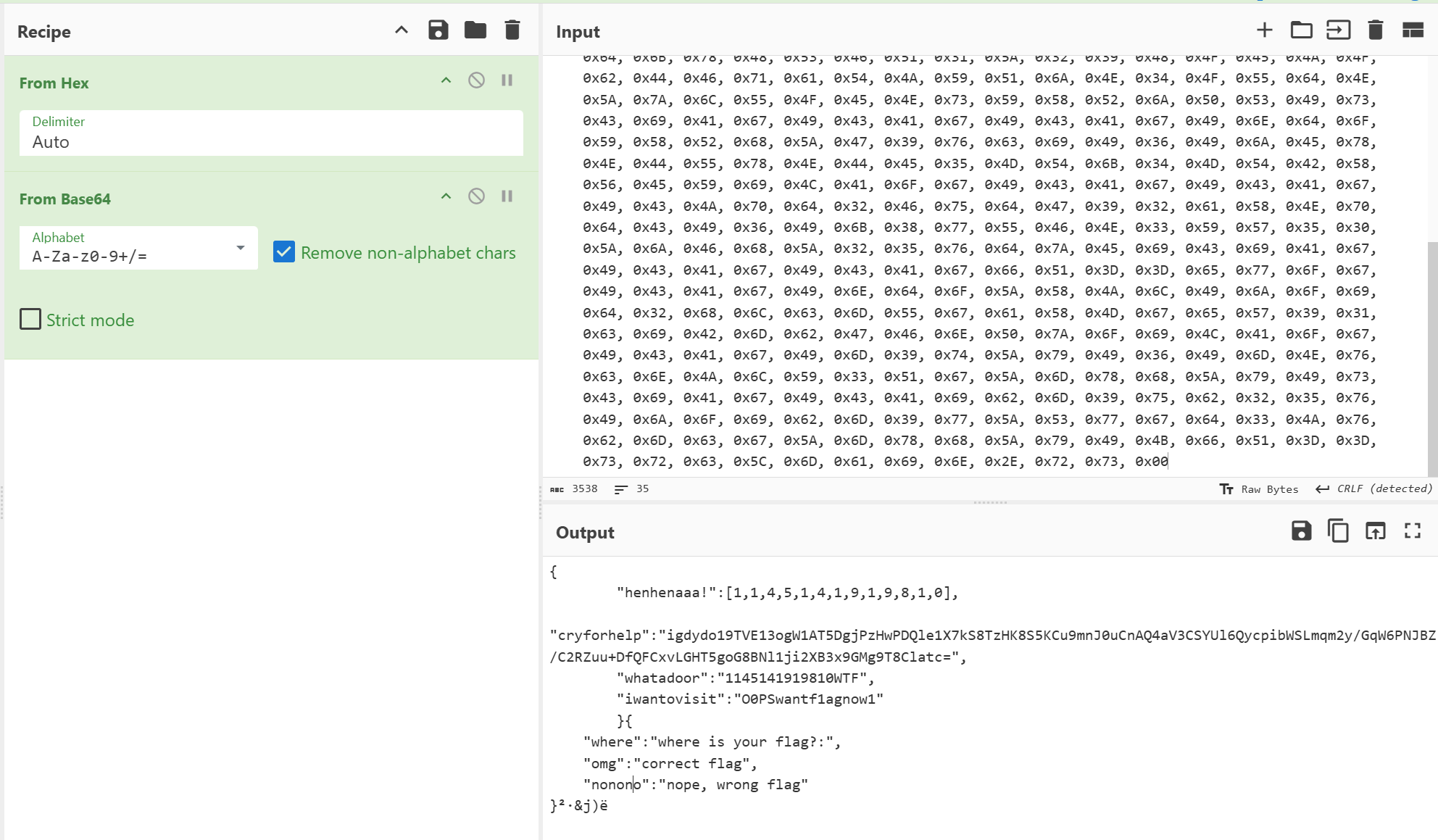
先写了个列表,然后慢慢从列表中调用
动调看加密,先是一个补齐,一直补到104位,这里是第一步加密,取8个字节,一个sub_1400028C3,一个异或
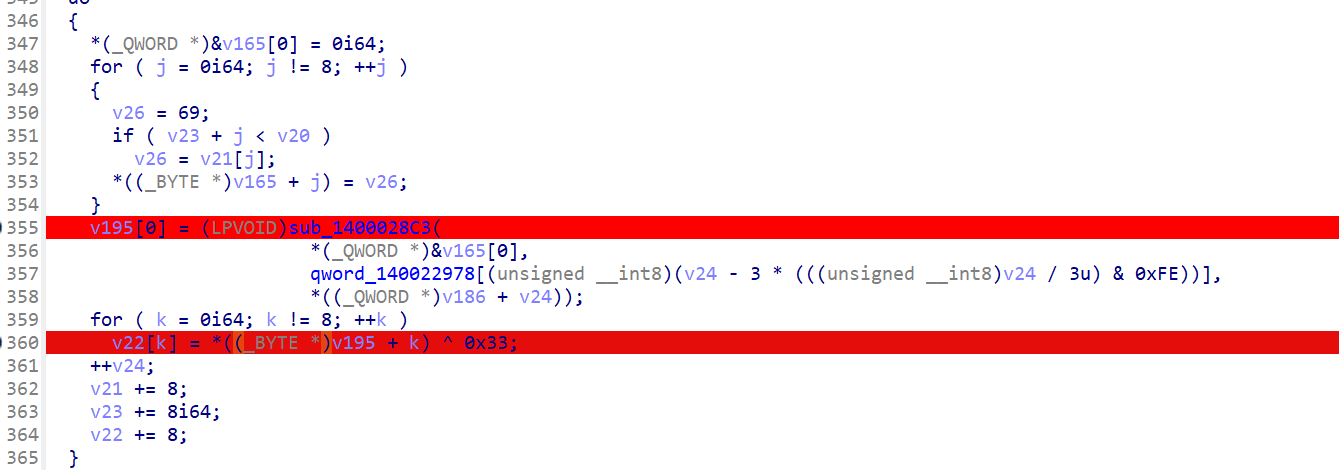
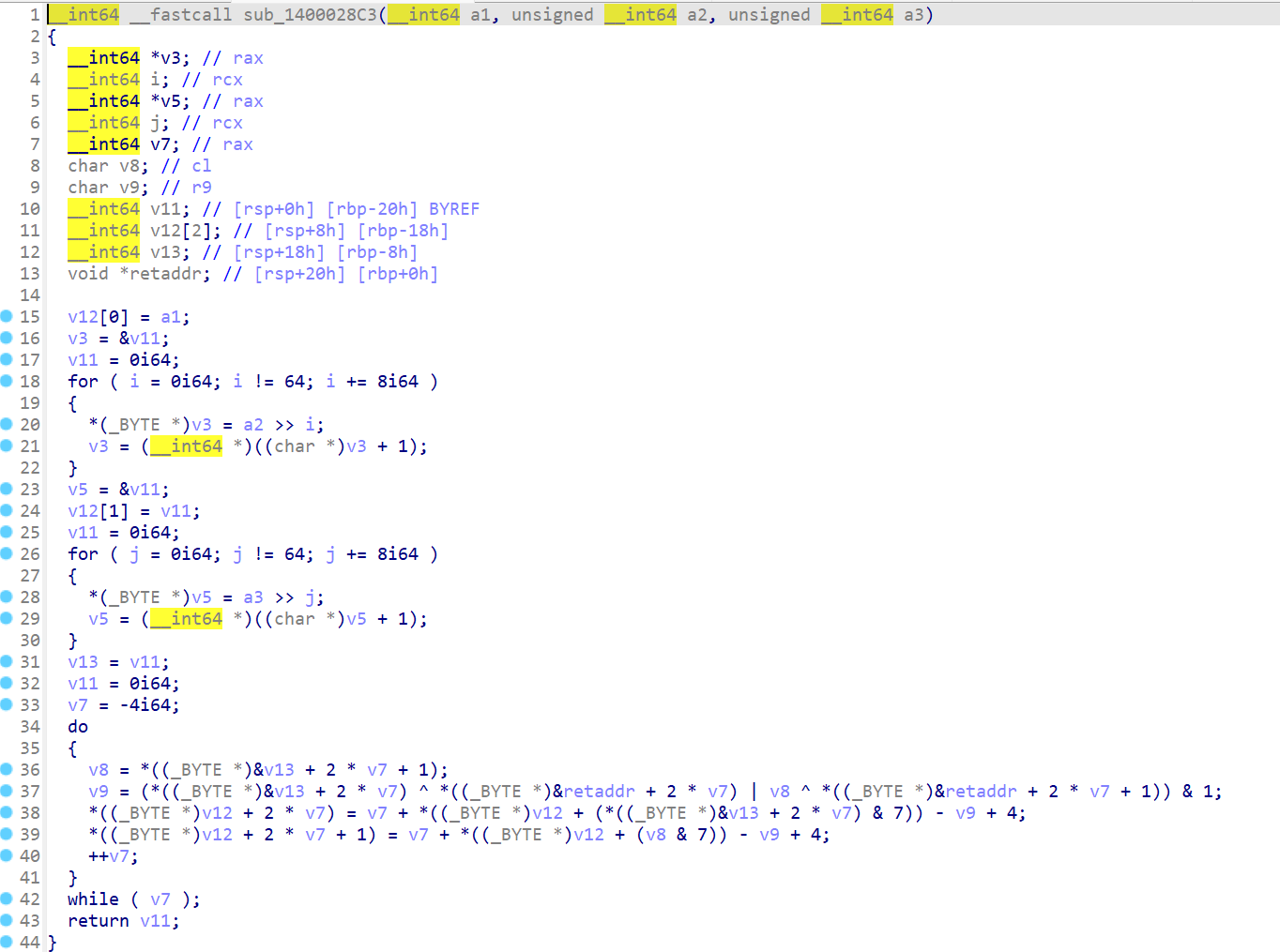
进去看不懂,但是根据输入输出进行大概猜测就知道是-1,0,+1,+2操作
后面进行16个字节分组,下一步加密是在这里,异或v96的表,这个表每次循环都会换一下,但是直接动调取就行
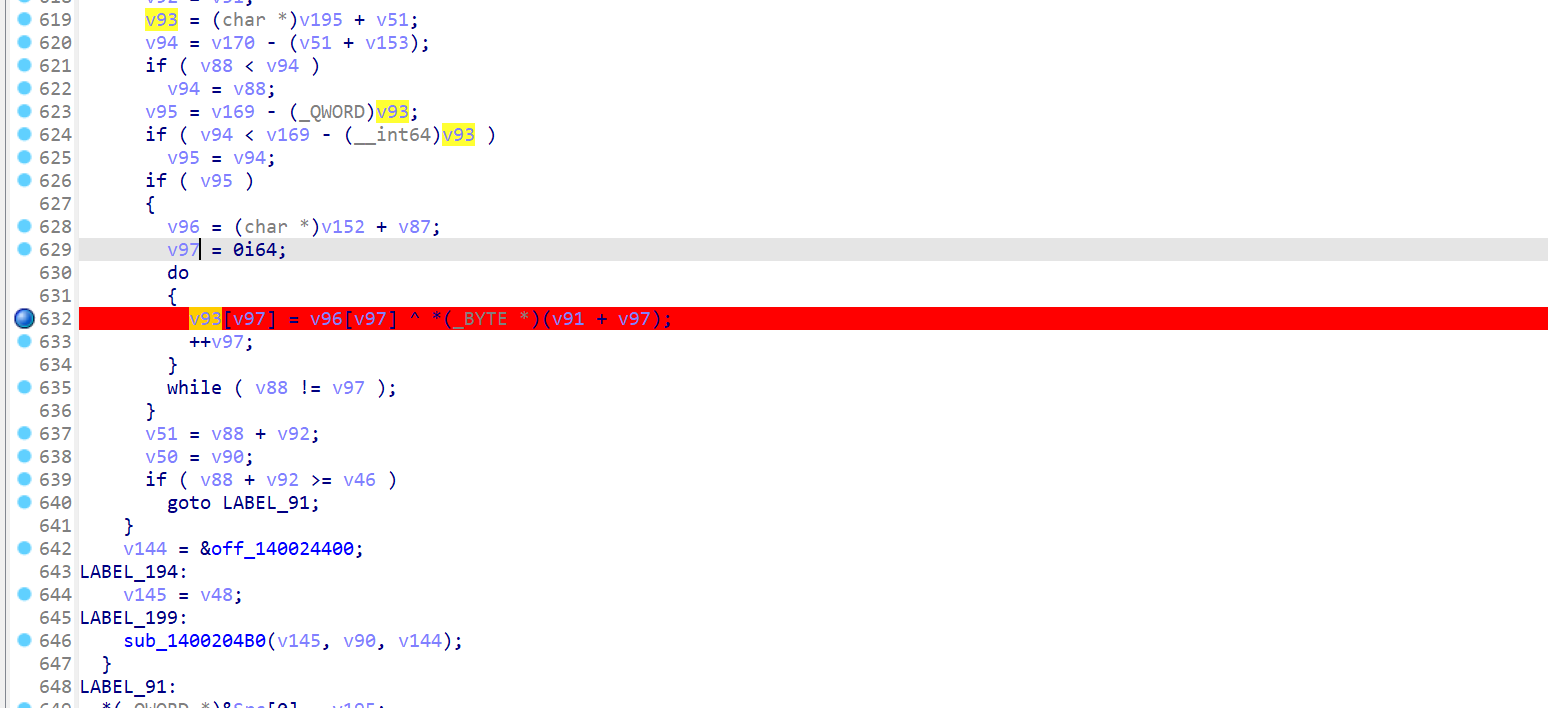
一直到比较段,都没咋动,下面一大串都没啥用
然后写个脚本出
1 | pw = [0x8a,0x07,0x72,0x76,0x8d,0x7d,0x4d,0x51,0x35,0xde,0x88,0x16,0xd4,0x04,0xf9,0x0e,0x08,0xcf,0xcc,0x7c,0x0f,0x0d,0x09,0x5e,0xd5,0x7e,0xe4,0x4b,0xc4,0xf3,0x1c,0xaf,0x12,0xe4,0xa0,0xae,0xf6,0x69,0xc9,0xd2,0xe0,0xa7,0x01,0x0e,0x1a,0x57,0x70,0x92,0x61,0x49,0x7a,0x43,0x27,0x29,0x89,0xb5,0x92,0x2e,0x6a,0xa6,0xdb,0x2f,0xc6,0xa9,0x6e,0x8f,0x34,0x90,0x59,0xfc,0x2d,0x91,0x66,0xeb,0xbe,0x0d,0xf4,0x05,0x0b,0x1b,0xcb,0x18,0x74,0xf9,0x82,0x81,0xbc,0x04,0xd9,0x75,0x8e,0x2d,0x97,0x07,0x7c,0x7d,0x18,0xc8,0x3d,0x4f,0xc0,0xa5,0x6a,0xd7] |
whereThe1b
一个python写的lib,base32,各种随机数异或调用啥的,看了一会不想看了,发现是分组加密,三位对应四位,而且是可见字符,直接放在虚拟机(因为好像只有linux能调用cpython)里爆破了
1 | import whereThel1b |
Goreverse
思路超级清晰,就是加密嵌套太多层了,只要一出错就得还原重新看,sm4那里就是死活出不来,最后才知道是iv搞错了,真无语了,这题调试还是一坨,调一步卡一步,有两个反调试。最后看vidar-team的wp复现的。
先用go脚本还原一下大部分符号名
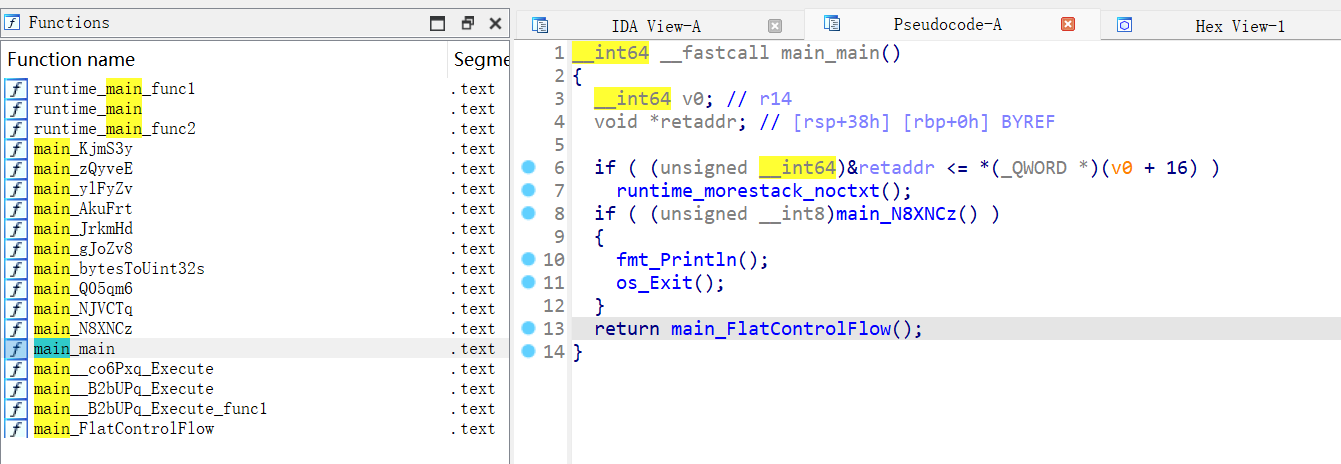
main函数一个反调试,直接把exit()nop掉就行,继续运行到
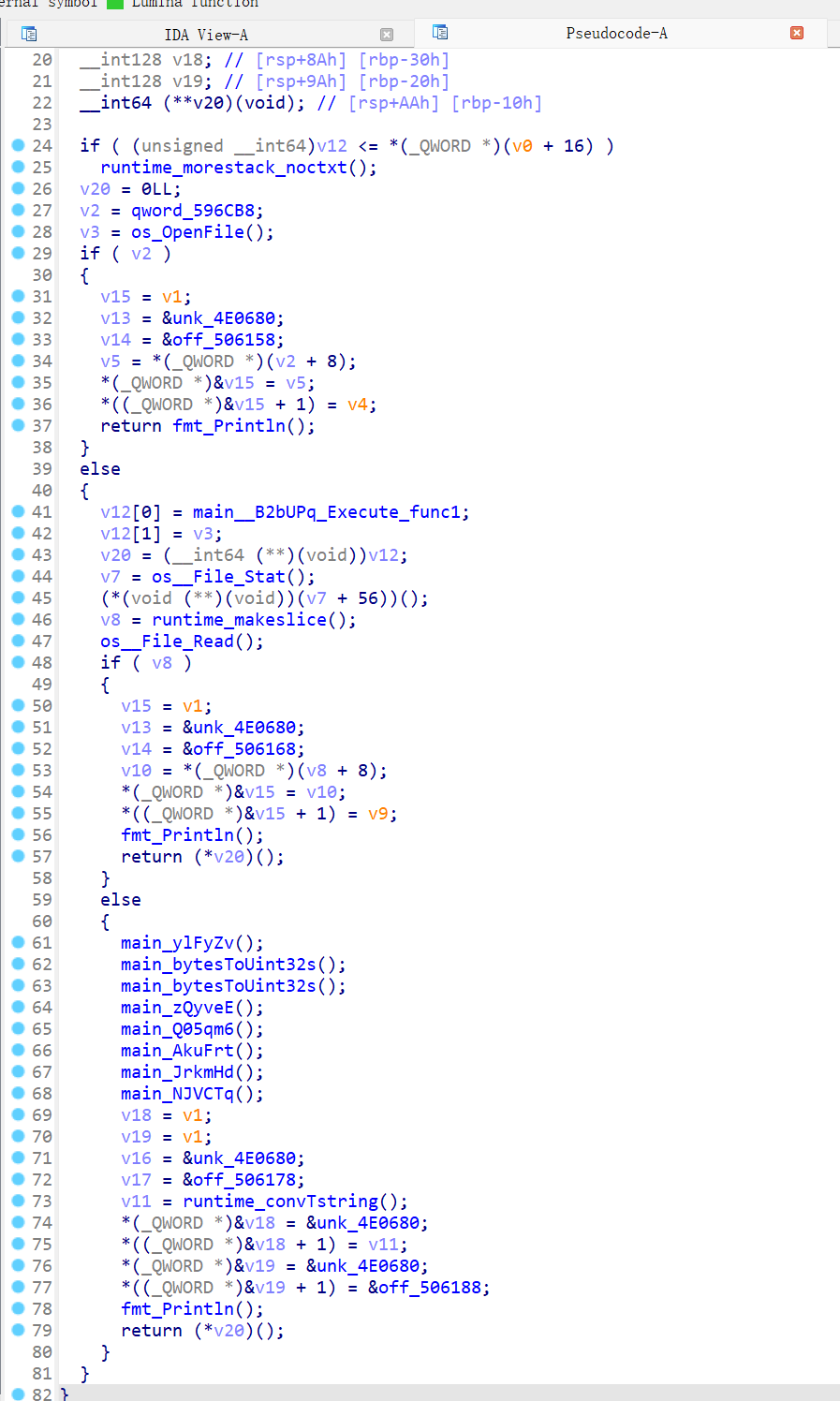
很明显一个open了一个flag文件读入,然后进行以下几个操作,逐步分析
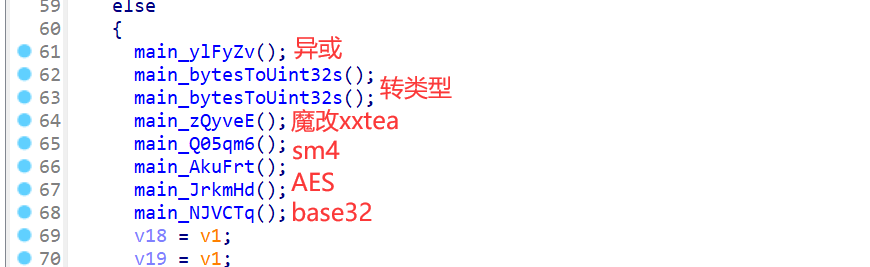
大概就是这样,找到aes的key和iv,然后找到sm4的key和iv,还原xxtea算法和找到xxtea的key,找到异或表,就可以穿了。。。
1 | char table[]="D7BJLsOk9@f&1dWIn53IDlJqUS6$^WhkAk2kk*2GaqmLwiLX^bGGE$&dmqR^g5bL3"; |
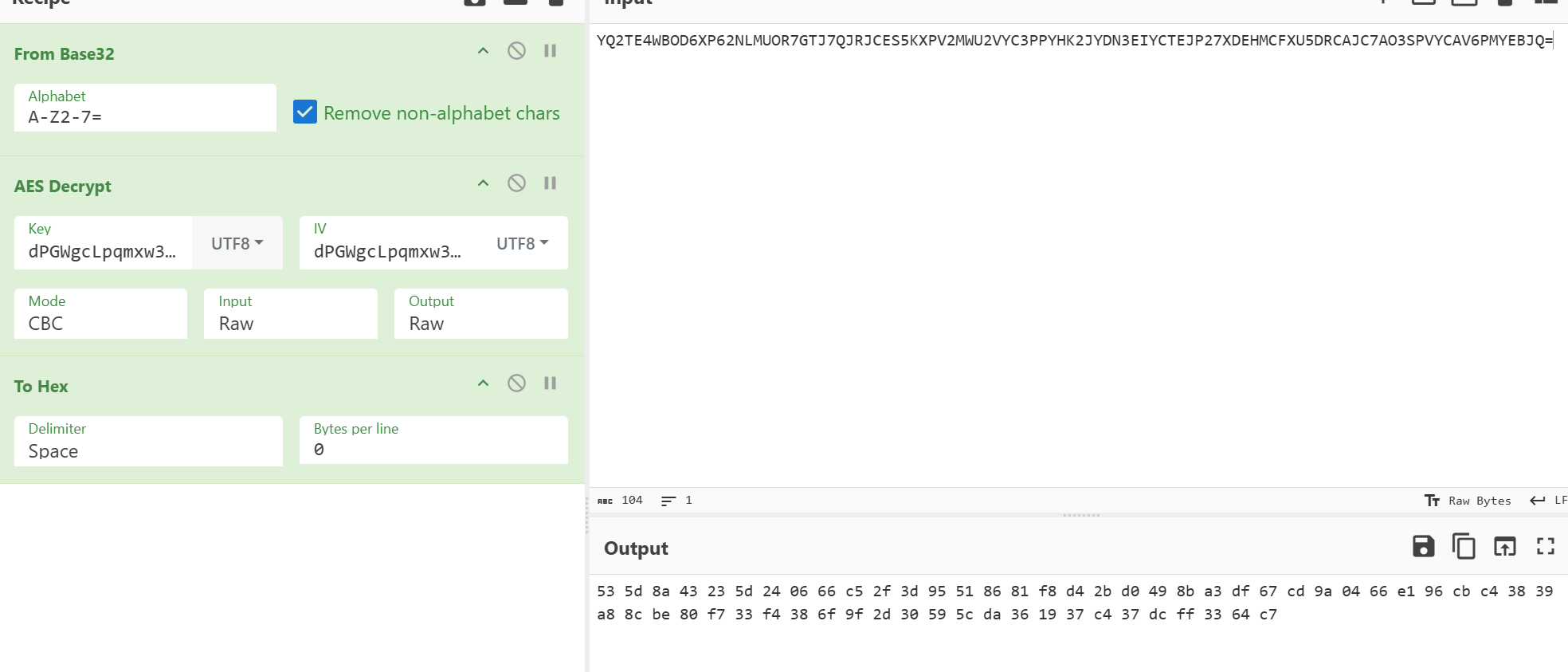
输出的前16个字节是sm4的iv,后面的都是sm4的密文,因为进行加密的iv是随机数,只能通过这个方法判断
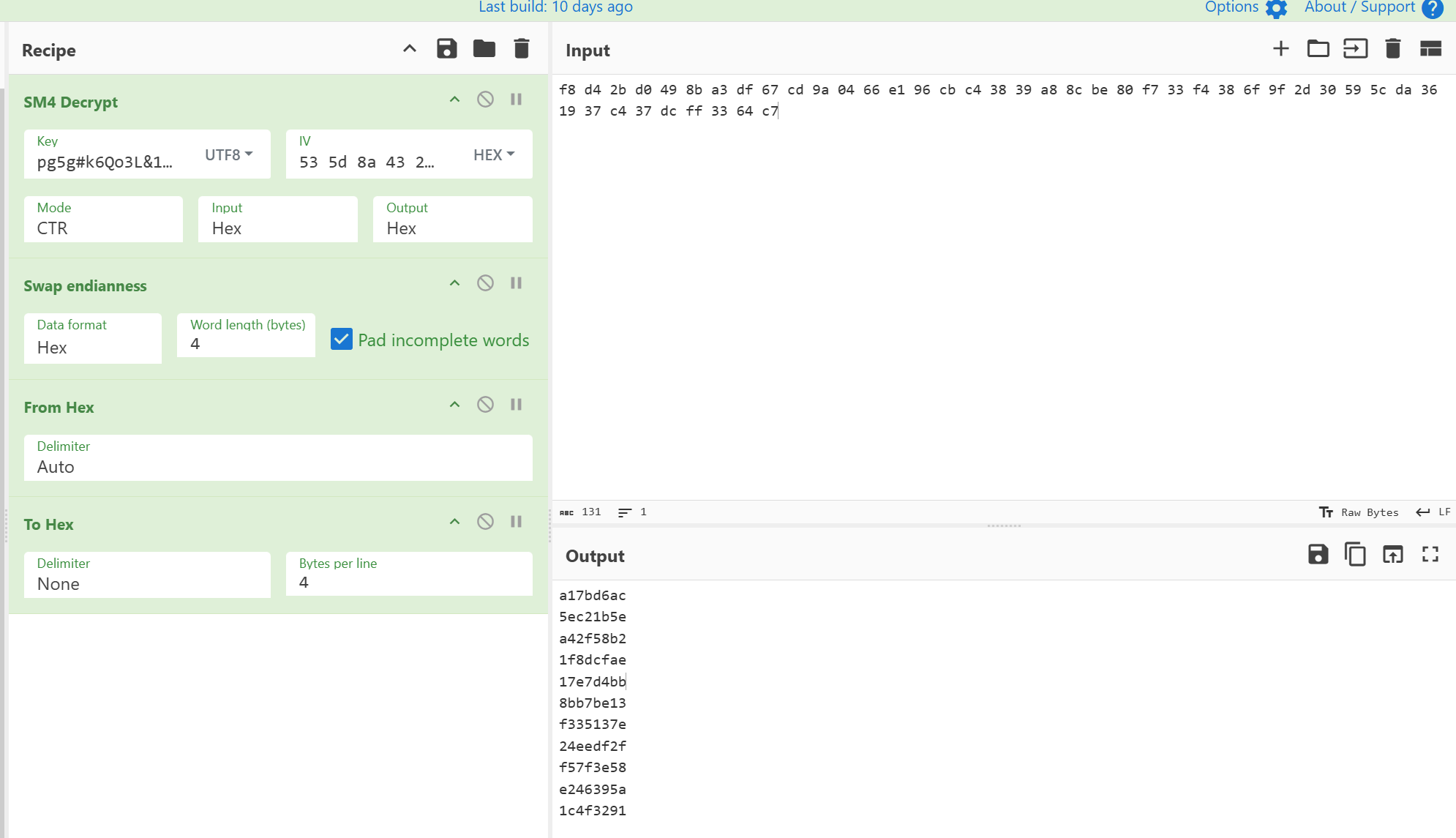
最后再进行一步xxtea解密和异或表
1 |
|
gdb_debug
固定的种子,一共调用了三次,先把需要用的rand值全部打印出来成为一个表,然后加密就是简单的异或+换表顺序+异或,写个脚本出了,第二天的签到。。。
1 |
|